[redacted] keeps you up to date on your security posture anytime, anywhere.
Get real-time insight to help you level the playing field against attackers.
Visibility into the security investigation process
View what [redacted] is taking care of and know what to do next
Insights into attack patterns to stay ahead of potential threats
Schedule a call with a member of our cyber defense.
[redacted] respects your privacy. For more information,
see our Privacy Policy.
Speak with our Cloud Security Technology team.
Monitor & Compare changes in your security.
View changes over time and compare yourself with others to gain a clear picture of your security posture.
View where potential threat sources originate
Know what actions are being taken to keep you safe in real-time
Track how changes are taking place over time
Alerts
When something happens, be the first to know.
-
Know what's happening on your network.
We notify you of what’s most important to you and your organization so that you can stay focused on what matters.
-
When we find something, we take pursuit.
We disrupt your adversaries, tracking them down to hold them accountable and keep you informed along the way.
Personal
Connect with humans behind your cyber defense.
-
Communicate directly with the people responsible for your security.
Through different phases of the process, we will connect you to those handling your issue so you can speak to the right person at the right time.
-
Analytical guidance from the world's top security experts
Demystify complex technical situations directly with the team responsible.
Insights
Stay one step ahead of the attackers.
Get insights into attack patterns to get ahead of potential threats and level the playing field against attackers.
Network
Track & Secure your network assets.
-
Know where your network stands.
Monitor the status of all your assets and be alerted when critical incidents arise.
-
Heighten your strengths, bolster your weaknesses.
Know where your network health stands, improve the security of your network.
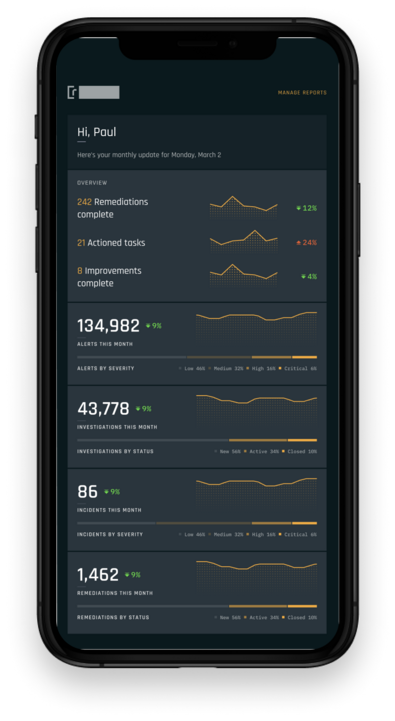
Reports
Defense data crafted to your needs.
-
Custom reports tailored with the data most important to you.
Build the reports you need to track all your cyber defense data while on the go.
-
Scheduled reporting to keep you in the loop.
Schedule your reports to know your security posture over time.

Keep your company from experiencing a security nightmare
Cyber threats are not only complex, they're ever-changing. No matter how prepared you think you are, at some point attackers will get in. Without the right partner, a cybersecurity mishap could cost your business everything. Leverage the industry-leading experts at [redacted] and have peace of mind knowing your security is in the best hands.


