[r In the News
The FBI and friends have warned organizations to “strictly limit the use of RDP and other remote desktop services” to avoid BianLian infections and the ransomware gang’s extortion attempts that follow the data encryption.
Cyber activity since the invasion shows the difference between peacetime and wartime attacks. Read Adam Flatley’s article on the Russo-Ukraine war’s impact on cybersecurity and the need to bolster defenses against attacks such as NotPetya.
[r Press Releases
Former NSA Director of Operations Appointed as Vice President of Intelligence; Will Lead Team Delivering Actionable Threat Intelligence to Customers AUSTIN, Texas–(BUSINESS WIRE)–[redacted], the mission-driven cybersecurity company that levels the playing field against attackers, today announced that Adam Flatley has been promoted to Vice President of Intelligence leading the [redacted] Intelligence Cell, recently renamed [rTIC Ghost Group. The team of battle-hardened cybersecurity and intelligence experts focuses on technical and human intelligence collection, analysis, and production.
[redacted] Continues Leadership Team Growth with Appointment of Aaron Ansari as Chief Revenue Officer 20-Year Industry Veteran with Deep Security Experience Joins [redacted] to Accelerate Sales Growth AUSTIN, Texas – August 8, 2022 – [redacted], the mission-driven cloud defense company that levels the playing field against attackers, today announced the appointment of Aaron Ansari as Chief Revenue Officer. In this newly created role, Aaron will lead [redacted]’s sales and marketing organizations as the company continues its rapid growth and expansion.
AUSTIN, Texas – July 11, 2022 – [redacted], the mission-driven cloud defense company that levels the playing field against attackers, today announced the appointment of Jim Hansen as CEO. With the addition of Hansen to the executive team, [redacted] co-founder and former CEO Max Kelly will elevate his role to executive chairman. Max will work with Jim to continue driving the company’s mission of providing the advanced product-enabled solutions required for organizations of all sizes to proactively defend themselves against nation-state attackers.
SAN FRANCISCO – June 7, 2022 – [redacted], the mission-driven cloud defense company that levels the playing field against attackers, today made its Threat Intelligent Detection Engine [TIDE] available to the public for testing and community-driven extensibility. [TIDE] is a binary analysis platform built by security practitioners for security practitioners. As an integrated piece of [redacted]’s cloud-native platform, [RIP//TIDE], which scales delivery of its layered defense services, [TIDE] automates the technical analysis of all files and immediately shares results with clients.
SAN FRANCISCO – June 7, 2022 – [redacted], the mission-driven cloud defense company that levels the playing field against attackers, today announced a partnership with ByteChek, the all-in-one compliance automation company that simplifies cybersecurity compliance for companies of all sizes. Through the alliance, [redacted] is using the ByteChek platform to significantly streamline SOC 2 and HIPAA compliance audits as part of its tailored cybersecurity services. In addition, ByteChek customers who require help with remediation or implementation of compliance audit results will use [redacted] as a preferred service provider.
SAN FRANCISCO – March 21, 2022 – [redacted], the mission-driven cloud security company that levels the playing field against attackers, today announced that it has been named to the Forbes list of America’s Best Startup Employers. This prestigious award recognizes the top 500 high-growth companies with exceptional culture and work environments. “We are honored to be recognized by Forbes as one of the top employers in Security,” said Max Kelly, co-founder and CEO of [redacted].
SAN FRANCISCO – February 15, 2022 – [redacted], the mission-driven cloud security company that levels the playing field against attackers, today announced the appointment of Tim Kosiba as Chief Executive Officer of bracket f, Inc., a wholly owned subsidiary of [redacted] focused on the government market. In this newly-formed position, Kosiba will forge trusted partnerships with organizations across federal, state and local governments by providing the services, solutions, and training required to mount an effective defense against cyberthreats.
SAN FRANCISCO–(BUSINESS WIRE)–[redacted], the mission-driven cloud security company that levels the playing field against attackers, today launched the Threat Intelligent Detection Engine (TIDE). As a major expansion of its cloud-native platform that scales delivery of [redacted]’s layered defense services, TIDE automates the technical analysis of all files and immediately shares results with clients. “Not only does this empower our clients in their SOC, it also provides structured interaction for our team members to provide orchestrated response.
SAN FRANCISCO – November 17, 2021 – [redacted], the mission-driven cloud security company that levels the playing field against attackers, today announced that it was selected by the American Hospital Association (AHA) as its Preferred Cybersecurity Provider for its incident response services. The company also was selected by the AHA for its Healthcare Security Services packaged offering that provides member hospitals with cyber program strategy and development and cyber risk assessment among other services.
SAN FRANCISCO–(BUSINESS WIRE)–[redacted], the mission-driven cloud security company that levels the playing field against attackers, today announced it has joined the ISA Global Cybersecurity Alliance (ISAGCA) as its newest founding member. The company will collaborate with fellow alliance members to explore ways to better secure automation and control systems that serve as the backbone of manufacturing and critical infrastructure. The Global Cybersecurity Alliance was established by ISA to advance cybersecurity readiness, education, and best practices in manufacturing and critical infrastructure facilities and processes.
SAN FRANCISCO – October 19, 2021 - [redacted] today announced that William Crowell, the former Deputy Director of the National Security Agency (NSA), has joined the company’s Board of Directors. In this role, Crowell will bring more than 50 years of security, technology, and intelligence experience in the public and private sectors to help guide [redacted] as the company accelerates adoption of its state-of-the-art platform and executes its mission to level the playing field for organizations against sophisticated attackers.
SAN FRANCISCO – August 02, 2021 – [redacted], the mission-driven cloud security company that levels the playing field against attackers, today announced that it has successfully completed the Service Organization Control (SOC) 2 Type 1 audit and certification, validating [redacted]’s commitment to customer data security. The independent audit, conducted by Moss Addams, LLP, focused on [redacted]’s internal controls and procedures related to security, availability, processing integrity, confidentiality and privacy controls, based on compliance with the American Institute of Certified Public Accountants (AICPA) TSC (Trust Services Criteria).
SAN FRANCISCO – June 1, 2021 – [redacted] today emerged from stealth with $35M in Series B funding led by Ten Eleven Ventures, with participation from Valor Equity Partners and SVB Capital. The company will use the funding to scale and accelerate adoption of its state-of-the-art platform and advanced threat intelligence and response capabilities that enable organizations to level the playing field against sophisticated attackers, disrupt their adversaries and protect their businesses.
[r Newsroom Archive
Researchers are unraveling the threads connecting two separate, but in some ways overlapping, Russian-language APTs.
Ransomware activity increased in February according to the latest GRIT Ransomware Report from GuidePoint Security. The report is based on data collected by the GuidePoint Research and Intelligence Team, which reports a 51.5% increase in attacks compared to January and a 15.8% increase in attacks compared to February 2022.
The BianLian ransomware group burst onto the hacking scene with a frenzied pace of operations. Its infrastructure goes back to 2021, but it was August of last year that saw the group enter an accelerated growth phase, with a number of high-profile ransomware attacks across the globe, including in Australia.
Not all ransomware groups wield crypto-locking malware. In their continuing quest for extortionate profits, some have moved away from encryption and pressure victims purely by threatening to leak stolen data unless they receive a ransom payment.
Security is a shared responsibility between MSSPs and their clients. Yes, the provider was hired to do a job – be it SOC operations, threat intelligence or offensive security – but part of the job is also to consult and communicate with the client to help them gain some degree of cyber self-sufficiency. This discussion will reveal how providers can teach their clients how to develop a secure corporate culture, how to share responsibility and accountability for security matters, and how to broaden their security awareness through partnerships with professional development organizations and information sharing groups.
The shift in the operating model comes as a result of Avast’s release of a decryption tool that allowed a victim of the BianLian ransomware gang to decrypt and recover their files without paying the ransom.
A ransomware(opens in new tab) group known as BianLian has decided to part ways with its encryptor and focus solely on data theft and extortion instead, experts are reporting. A new report from cybersecurity researchers Redacted spotted BianLian attempting to extort businesses for money - without encrypting their endpoints first.
BleepingComputer reports that the BianLian ransomware gang has transitioned to pure data extortion and ditched data encryption efforts in its most recent attacks following the emergence of a free ransomware decryptor in January.
The BianLian gang is ditching the encrypting-files-and-demanding-ransom route and instead is going for full-on extortion.
Financial Scams, Microsoft, BianLian, Leihigh Medical, CISA, Vile, and More on this episode of the Security Weekly News!
A DC health insurance service breach has compromised information of Capitol Hill members and staffers. What could a breach impacting lawmakers mean for the outlook on national cybersecurity?
Google has announced plans to reduce the maximum lifespan of a TLS certificate from the current value of 398 days to only 90 in a move that is going to send shockwaves across several IT industries.
The personal data of millions of Australians may be at risk after cyber criminals stole a reported 1TB of data from Parques Reunidos, a Spanish theme park operator whose multinational portfolio of properties includes Sydney’s popular Raging Waters park.
The ransomware group has already claimed 116 victim organizations so far on its site, and it continues to mature as a thriving cybercriminal business, researchers said.
The Ukraine war has inspired a defensive cyber effort that government officials and technology executives describe as unprecedented.
New York’s Suffolk County began restoring online services and reconnecting its systems to the internet this month, according to CBS News. It comes five months after being taken offline due to a ransomware attack. The time it took to restore services speaks to how prepared both the government and the private sector should be to respond to ransomware attacks, as well as the need to bring tangible consequences to the threat actors who steal critical data.
Tallahassee Hospital in Florida was forced to cancel all non-emergency surgical and outpatient appointments, diverted some EMS patients and began accepting only the most serious trauma patients following a cyber incident. [redacted] VP of Intelligence Adam Flatley tells Jeffrey Burlew at the Tallahassee Democrat that the incident is “definitely following the pattern of what looks like a ransomware attack.”
Adam Flatley, director of threat intelligence at cybersecurity firm Redacted said cyber-threat actors attack healthcare organizations on a regular basis because they know the “emotional impact” will help force an extortion payment.
[redacted] VP of Threat Intelligence Adam Flatley spoke with Sam Sabin of Axios on the recent HIVE ransomware takedown by US-German law enforcement. According to Adam, despite warnings from threat groups, organizations should be urged to contact federal authorities saying, “While many ransomware gangs threaten victims to not call the feds, the Hive operation shows the FBI is capable of discreetly helping victims.”
ChatGPT took the world by storm after OpenAI opened it for testing on Nov. 30, 2022. For an industry calloused by years of largely unsatisfying AI and machine learning “innovations,” the reactions have been quite telling.
Last week, officials announced that US-German law enforcement took down the notorious Hive ransomware gang, thwarting $130 million in demands for payment from more than 1,500 victims around the world, which included hospitals, schools, financial firms and critical infrastructure. [redacted] VP of Intelligence Adam Flatley says to The Record’s Jonathan Greig that the most likely scenario is that the group will suffer a short-term disruption in operations due to the loss of infrastructure, conduct an internal security review to assess damage and update security practices, and then get back to business as soon as possible because there is just too much money to be made in ransomware.
U.K.’s Royal Mail service was hit by an alleged ransomware attack. The organization is now urging customers to refrain from sending packages overseas. [redacted]’s VP of Intelligence Adam Flatley tells InformationWeek’s Carrie Pallardy that “The biggest lesson is that we can’t continue to try to solve the cybersecurity problem with a purely defensive mindset. We need to move forward with an approach that blends together the approaches of preventing what is preventable, responding quickly and effectively to what is not preventable, and actively hunting down malicious cyber actors.
The country of Vanuatu is the latest victim in a string of crippling ransomware attacks on small countries this year. Experts say various motives underlie these incidents but disagree on whether this trend reflects a shift in threat actors away from well-resourced Western nations.
The second meeting of the U.S. Joint Ransomware Task Force held on Wednesday assessed measures and efforts to address the impact and prevalence of ransomware attacks.
A hacking group linked to the Chinese government is alleged to have stolen more than $20 million in COVID relief benefits, including U.S. Small Business Administration loans and unemployment funds in more than a dozen states.
Industry weighs in on proposed rules for how critical infrastructure organizations should report hacks to the government, and state attorneys general reach a settlement with Google over location tracking.
Speedy, practiced response is key to prevent, mitigate and recover from cyberattacks, say federal regulators amid an uptick in ransomware incidents affecting the healthcare industry.
In this episode of Healthcare is Hard, Tim Kosiba, CEO bracket F and former senior government official whose career spans three decades in the Department of Defense, the U.S. Department of the Navy, and the Federal Bureau of Investigation (FBI), shares some of his insider knowledge with Keith Figlioli on topics of growing urgency for everyone in the healthcare industry – from providers, payers and life science companies, to the innovative startups transforming healthcare.
Healthcare organizations should consider how they plan for natural disasters such as hurricanes as they prepare for disruptive cybersecurity events such as ransomware attacks, says Paige Peterson Sconzo, director of healthcare services at security firm Redacted Inc.
BianLian is a relatively new threat actor that targets a wide range of industries. As they are likely financially motivated, they will continue their efforts to exploit systems and networks they gain access to.
Patient care continues to be disrupted at the U.S.’s fourth-largest hospital system as its response to a cyber incident enters a second week.
A new ransomware group operating under the name BianLian emerged in late 2021 and has become increasingly active since. [redacted] responds.
Cyber defense training for businesses is evolving to create immersive scenarios putting board members and C-level executives in the crosshairs of simulated attacks. Researchers at cybersecurity firm Redacted said in a report Thursday that the BianLian ransomware gang tripled its known operational infrastructure in August, indicating that more attacks from the gang could be coming soon.
The threat actors behind the BianLian Ransomware are rapidly expanding infrastructure, and it has been observed targeting manufacturing organizations.
Newly identified ransomware group BianLian has bolstered its command-and-control infrastructure, indicating increasing activity, The Hacker News reports. Fifteen organizations have already been impacted by BianLian ransomware since its emergence in mid-July, according to a report from cybersecurity firm [redacted].
A new ransomware group operating under the name BianLian emerged in late 2021 and has become increasingly active since. [redacted] responds.
BianLian, written within the Go programming language, was first found in mid-July 2022 and has claimed 15 sufferer organizations as of September 1, cybersecurity agency [redacted] stated in a report shared with The Hacker News.
The operators of the emerging cross-platform ransomware BianLian increased their command and control infrastructure this month, indicating an acceleration in their operational pace.

The operators of the emerging cross-platform BianLian ransomware have increased their command-and-control (C2) infrastructure this month, a development that alludes to an increase in the group’s operational tempo.
Federal authorities are sounding the alarm for the healthcare industry over Russian cybercrime gang Evil Corp, warning that the group has a wide set of highly capable tools at its disposal for taking healthcare data hostage.
Whether a business uses technology to manage operations, builds tech tools for other businesses or consumers, or both, it faces the risk of a cybersecurity breach on a daily basis. A successful hack can potentially expose a company’s sensitive data, damage its reputation or even shut down its operations altogether. A top priority for any company working with technology and data must be a robust incident response plan.
The Department of Justice is investigating a data breach of U.S. court records dating back to 2020, raising concerns that federal investigations could be compromised.
Ukraine claims to have taken down a massive Russian bot farm. Were Russian cyber operations premature? Adam Flatley from [redacted] with a look back at NotPetya.
The US authorities have managed to return half a million dollars to several corporate victims, including healthcare providers forced to pay up after being infected by a new ransomware strain. Tim Kosiba, [redacted] bracket f CEO, urges healthcare providers to stay alert.
Companies should be wise to assume that a second Cold War is upon us and that they—depending on their company’s size, industry and partnerships—are among the prime targets.
Redacted gains CEO who has threat response, phishing cyberattack prevention and SOAR expertise from Mandiant, Cofense and Swimlane.
The FBI has identified a state-sponsored ransomware campaign targeting critical services in the US and has warned organizations to be prepared. Adam Flatley, director of Threat Intelligence at [redacted], responds.
[TIDE] is a binary analysis platform built by security practitioners for security practitioners. As an integrated piece of [redacted]’s cloud-native platform, [RIP//TIDE], which scales delivery of its layered defense services, [TIDE] automates the technical analysis of all files and immediately shares results with clients. By now opening the platform for public access, [redacted] is creating a modular ecosystem that greatly expands the volume of binary files available to search and explore.

It is with excitement and gratitude that IST announces new funding support and acknowledges the key financial supporters of the Ransomware Task Force at the beginning of its second year.
“[redacted] (the company’s actual name is [redacted], Inc.), a cyber defense company, has just appointed a former Deputy Director of the National Security Agency to the company’s board. William Crowell has been active in the field of public and private information security for decades”
Companies hit by hackers typically limit themselves to playing defense to comply with a federal law against invading someone’s computer. But some specialist cybersecurity firms say they can pursue criminals without launching their own attacks. Most cybercrimes in the U.S. fall under the Computer Fraud and Abuse Act, a 1986 law that prohibits unauthorized access of computer systems. The law effectively places offensive cybersecurity actions solely in the hands of the federal government.
Twitch is breached. A newly discovered Iranian threat group is described. A Chinese cyberespionage campaign in India proceeds by phishing. SafeMoon alt-coin is trendy phishbait in criminal circles. As the US prepares to convene an anti-ransomware conference, Russian gangs show no signs of slacking off. Betsy Carmelite from BAH on AI/ ML in cyber defensive operations. Our guest is Adam Flatley of [redacted] with recommendations from the Ransomware Task Force. And observations on what counts as compromising material.
Ransomware extracted $18 billion in payments last year, and it’s expected there will be an attack every 11 seconds by this year’s end, a problem that some security experts and academic researchers say is exacerbated by the system meant to protect against cybercrime: the insurance industry. Organizations with cyberinsurance are more than twice as likely to pay ransoms as those without, according to a global survey commissioned by U.K.-based cybersecurity and software firm Sophos of 1,823 companies, governments, health systems,…
Organizations with cyberinsurance are more than twice as likely to pay ransoms as those without, according to a global survey commissioned by U.K.-based cybersecurity and software firm Sophos of 1,823 companies, governments, health systems, and other organizations that had been hit by ransomware. This is one of the first times such data have been gathered that show the extent of the relationship between cyberinsurance and ransomware payments. Critics say that relationship helps fuel a ransomware economy that the federal government estimates causes $445 billion in damages to the global economy every year.
If your data center’s ransomware recovery plan is to pay off the hackers with cryptocurrency, it’s time to rethink your strategy as regulators crack down. Today, every data center manager should be aware of the dangers of ransomware and have a disaster recovery plan that doesn’t involve paying hackers’ ransomware demands.
The US Treasury has added a Russian cryptocurrency exchange to its sanctions list after claiming the firm helped facilitate ransomware payments for countless groups. SUEX is incorporated in the Czech Republic but reportedly operates out of Russia. The Treasury estimated that 40% of its transaction history is associated with “illicit actors.”
Infamous ransomware gang REvil has returned to the dark web, the shady corner of the internet reachable with special software, after disappearing in July amid pressure from the U.S. government on Russia to act on ransomware groups operating in the country. REvil, also known as Sodinokibi, was before its disappearance a prolific ransomware group linked to dozens of attacks. Its most high-profile attack before going dark involved targeting companies using information technology management software from Kaseya Ltd.
Nations have to stop sheltering bad actors in order to stop them, expert says. TechRepublic’s Karen Roby spoke with Adam Flatley, director of threat intelligence for [redacted], a cybersecurity company, about the future of cybersecurity. The following is an edited transcript of their conversation.
Paying ransom should be your last resort, cybersecurity expert says Some organizations can get by without paying in a ransomware attack, but others really have no choice, he says.

Tonya Hall talks to Adam Flatley, director of threat intelligence at Redacted Inc.,about what has been missing in anti-ransomware plans.
Tonya Hall interviews Adam Flatley, director of threat intelligence at Redacted Inc., about the options businesses have when facing a ransomware attack
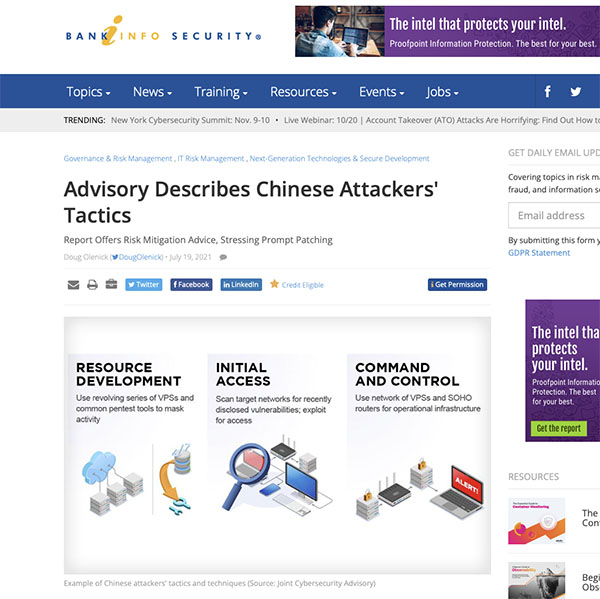
Three federal agencies released a 31-page Joint Cybersecurity Advisory Monday that describes 50 tactics, techniques and procedures that Chinese state-sponsored cyberattackers are using to target organizations in the U.S. and allied nations. The Chinese attack techniques outlined in the report include exploiting well-known vulnerabilities in widely used applications, such as Pulse Secure, Apache, F5 Big-IP and Microsoft products.
The State Department announced a $10 million reward for any information about hackers working for foreign governments. The measure is aimed squarely at those participating in “malicious cyber activities against US critical infrastructure in violation of the Computer Fraud and Abuse Act.” Officials said in a release that this included ransomware attacks targeting “critical infrastructure.”
Yesterday’s noisy raid of the Clop ransomware gang in Ukraine was a major win according to most experts throughout the cybersecurity community, who said the moment marks a shift in the international war on ransomware. The raid, according to Ukrainian reports translated by eSpire analysts, included the arrests of six people in Kiev, the seizure of $185,000 in cash, a Tesla, a Mercedes and their computer equipment. Those arrested face up to eight years in prison, the records s
President Biden and his team have warned the Putin administration of 16 critical infrastructure entities that are off-limits for threat actors operating from Russia. The news came as the two leaders sat down in Geneva for a summit which Biden said was designed to ensure a “stable and predictable” relationship between countries following the turmoil of the Trump years.
Former Facebook CSO, NSA and CIA Operatives Team Up to Level the Playing Field for Organizations against Attackers
Today a startup called [redacted] is coming out of stealth with a different approach to tackling malicious activity — it applies threat intelligence, and then proactively goes after the hackers to recover data loss and disrupt their activities
San Francisco-based cybersecurity provider [redacted] officially emerged from stealth with a $35 million Series B to help small and medium-sized businesses be more secure.